Cybersecurity Compliance Regulations in the European Union (EU)

Cyberattacks are becoming more diverse in the EU, with phishing, web attacks, and DDoS attacks being common. Stolen credentials and business email compromise also pose significant threats. While financial gain is a major motive, many attacks aim to plant spyware or deploy ransomware.
A recent Cloudflare study on cybersecurity in Europe found that in the past year, 40% of European organizations experienced a cybersecurity incident, with 84% of those affected reporting an increase in attack frequency. Alarmingly, 16% suffer a cyberattack every 6-11 days.
Yet, despite the rising volume and frequency of cyberattacks, only 29% of European organizations feel highly prepared to handle future incidents. The healthcare and education sectors are among the least prepared, while the IT and technology, financial services, and retail sectors show the highest level of confidence.
The EU has enacted robust cybersecurity regulations, such as the General Data Protection Regulation (GDPR) and the Network and Information Systems (NIS) Directive, to protect businesses, consumers, and critical infrastructure. We'll examine these and explain why it's important to comply.
EU compliance regulations: Importance and impact
Regulatory compliance ensures that organizations adhere to laws, regulations, and industry standards established by governments and regulatory bodies. In the European Union, compliance plays a crucial role in promoting transparency, accountability, security, and ethical business practices. It safeguards consumer rights, strengthens cybersecurity, and fosters trust while holding organizations accountable for their security posture.
EU compliance regulations cover data protection, cybersecurity, financial transparency, healthcare, and environmental sustainability. With evolving threatsâ€â€particularly in data privacy, IoT security, and 5G networksâ€â€the EU continuously refines its regulatory framework to mitigate risks and enhance digital resilience. Adhering to these regulations not only ensures legal operation within the EU but also protects businesses from severe fines, reputational damage, and operational restrictions.
Given the global influence of EU regulations, organizations outside the EU, especially in sectors like healthcare and finance, must also stay informed about these requirements to ensure compliance and seamless cross-border operations.
Benefits of EU regulatory compliance:

1. Legal protection: Avoid hefty fines and legal consequences.
2. Market access and competitiveness: Enhance trust and expand business opportunities in the EU.
3. Data security and privacy: Ensure compliance with strict laws like GDPR, safeguarding customer data.
4. Operational efficiency: Streamlined compliance processes improve risk management and business performance.
5. Regulatory alignment: Stay ahead of evolving EU standards and maintain long-term business viability.

Key EU cybersecurity organizations and their roles
- ENISA (EU Agency for Cybersecurity)
- EE-ISACs (European Energy – Information Sharing and Analysis Centers)
- ECSO (European Cyber Security Organization)
- CSIRTs/CERTs (Computer Security Incident Response Teams/Computer Emergency Response Teams)
- JRC (Joint Research Center)
- Stakeholder Cybersecurity Certification Group (SCCG)
Evolution of EU cybersecurity compliance regulations
The EU began shaping its cybersecurity strategy in the early 2000s, initially focusing on awareness and basic security principles. Over the past decade, regulations have expanded significantly in response to the growing sophistication and frequency of cyber threats.
- 2004: Establishment of ENISA – The EU established the European Network and Information Security Agency (ENISA) to support Member States with cybersecurity expertise.
- 2013: EU Cybersecurity Strategy – Introduced a framework for pan-European cooperation on cyber defense.
- 2016: Network and Information Security (NIS) Directive & GDPRâ€â€The first EU-wide cybersecurity law (NIS Directive) and the General Data Protection Regulation (GDPR) were adopted to enforce stringent standards for data protection and privacy, becoming enforceable on May 25, 2018.
- 2017: Trusted Information Security Assessment Exchange (TISAX) – Introduced as a global cybersecurity standard for the automotive industry.
- 2019: EU Cybersecurity Act (CSA) – Created a certification framework for ICT security and made ENISA a permanent EU agency.
- 2020: Digital Operational Resilience Act (DORA) Proposal – Published on September 24, 2020, as part of the EU Digital Finance Package. It was officially agreed upon in 2022 and formally adopted in 2023.
- 2020: NIS2 Directive Proposal – The European Commission proposed the NIS2 Directive on December 16, 2020, and EU lawmakers agreed to it in May 2022.
- 2022: NIS2 Directive Adoption – The revised NIS2 Directive was adopted to standardize cybersecurity measures across Member States.
- 2024: Cyber Resilience Act – Introduced security requirements for digital products, including IoT devices, to ensure market safety.

What are the different EU cybersecurity compliance regulations?
To strengthen cybersecurity, the EU has introduced key regulations setting strict security requirements, incident response protocols, and cross-border collaboration.
Here are the key regulations that aim to enhance resilience, protect sensitive data, and create a safer digital ecosystem across industries:
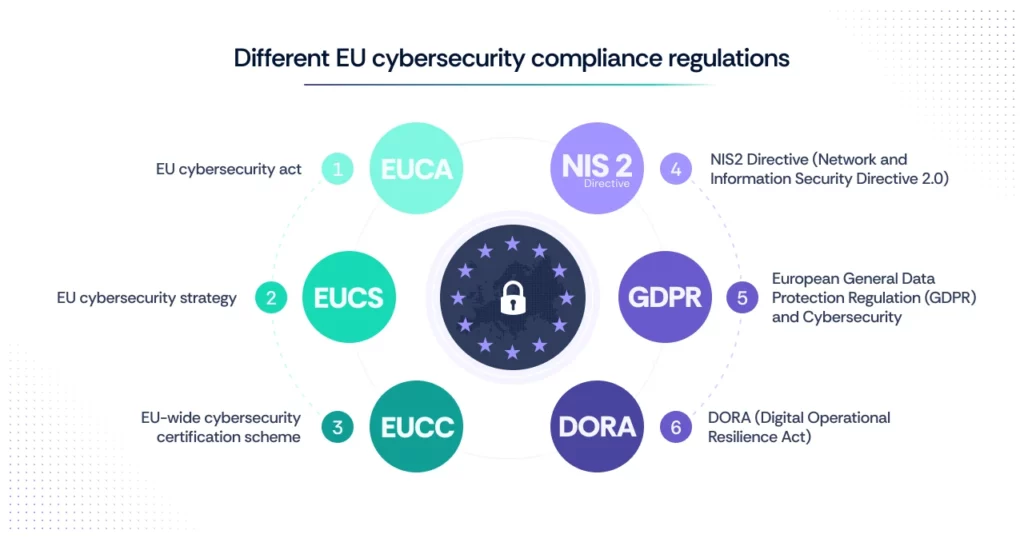
1. EU Cybersecurity Act
The EU Cybersecurity Act, introduced in June 2019, strengthens ENISA (the EU Agency for Cybersecurity) by granting it a permanent mandate, increased resources, and an expanded role in cybersecurity policy implementation. ENISA now oversees the EU-wide cybersecurity certification framework, provides guidance on certification schemes, and supports the coordination of cyber incident response across member states through the CSIRTs Network.
A key feature of the Act is the standardized cybersecurity certification framework, ensuring a single, EU-recognized certification for ICT products, services, and processes. This simplifies compliance, enhances trust, and facilitates trade across the EU.
A 2023 amendment proposal further intends to expand the Act's scope to include managed security services, such as incident response, penetration testing, security audits, and cybersecurity consultancy. This strengthens the security of critical digital services, improving cyber threat prevention, detection, and recovery.
2. EU Cybersecurity Strategy
In December 2020, the European Commission and the European External Action Service (EEAS) introduced a new EU Cybersecurity Strategy to enhance cyber resilience while preserving an open and secure digital economy. The strategy promotes EU cyber sovereignty, ensuring member states maintain control over their cybersecurity capabilities while protecting critical sectors like healthcare, energy, finance, and infrastructure.
Key legislative proposals under the strategy include:
- Revision of the NIS Directive (NIS 2 Directive) – Strengthens cybersecurity requirements for essential and important entities, enhances incident reporting, and improves cross-border cooperation.
- Critical Entities Resilience (CER) Directive – Expands protection for critical infrastructure against cyber and physical threats.
- EU Cyber Shield Initiative: This initiative focuses on establishing a pan-European network of Security Operations Centers (SOCs). These SOCs aim to leverage AI and advanced cybersecurity tools for real-time threat detection and response. It is a core part of the EU Cybersecurity Strategy to enhance cyber resilience across Member States.
- Joint Cyber Unit (JCU): Proposed in June 2021, the JCU is designed to coordinate operational responses to major cyber incidents. It serves as a collaborative platform for EU institutions, Member States, and private sector partners to streamline crisis response efforts and improve threat intelligence sharing.
Additionally, the strategy supports cyber diplomacy, increased investment in cybersecurity research and innovation, and the development of a secure European internet infrastructure (e.g., DNS4EU).
3. EU-wide Cybersecurity Certification Scheme
The EU-wide cybersecurity certification scheme, established under the EU Cybersecurity Act, ensures high security standards for ICT products, services, and processes while addressing regulatory barriers and market fragmentation. By providing a single certification framework recognized across all EU member states, it simplifies compliance, reduces costs, and enhances trust in digital solutions. Certification is voluntary (unless mandated explicitly by EU or member state regulations).
The scheme introduces three assurance levelsâ€â€basic, substantial, and highâ€â€to reflect the risk associated with cybersecurity threats and the intended use of ICT products. It also promotes transparency and accountability, helping businesses demonstrate compliance and strengthen their cybersecurity posture across the EU market.
4. Network and Information Systems (NIS) Directive
The Network and Information Systems (NIS) Directive, alongside GDPR, is a foundational EU-wide cybersecurity law that applies across sectors, including finance, energy, healthcare, and transport. As the first EU-wide directive aimed at strengthening cybersecurity and cooperation among member states, the original NIS Directive required implementation by May 2018.
The directive established security obligations for operators of essential services (OES) and digital service providers (DSPs) across three key areas:
- National capabilities – Requires member states to develop CSIRTs (Computer Security Incident Response Teams), risk management frameworks, and national cybersecurity strategies.
- Cross-border collaboration – Facilitates cooperation through the CSIRTs Network and the NIS Cooperation Group to improve EU-wide incident response.
- Supervision or enforcement by national competent authorities – Mandates cybersecurity oversight in critical sectors, ensuring organizations implement risk management measures and report significant incidents.
5. NIS2 Directive (Network and Information Security Directive 2.0)
The NIS2 Directive, which replaces the original NIS Directive, entered into force on January 16, 2023. EU Member States were to transpose it into national law by October 17, 2024). The NIS2 Directive significantly expands cybersecurity obligations across more industries, including healthcare, finance, energy, transportation, digital services, and public administration.
The directive strengthens cyber resilience across the EU by enhancing risk and incident management, broadening its regulatory scope, and improving cross-border cooperation. In May 2022, the Council and the European Parliament reached a provisional agreement, ensuring that member states oversee cybersecurity while collaborating to mitigate threats that could impact the entire EU.
Key enhancements in NIS2:
- Expanded scope – Covers more critical sectors and applies to medium and large companies, eliminating the previous distinction between essential service operators (OES) and digital service providers (DSPs).
- Stronger security and reporting requirements – Introduces a risk-based approach, requiring organizations to implement cyber risk management measures, including supply chain security.
- Faster incident reporting – Security incidents must be reported without undue delay ideally within 24 hours of detection, with a detailed report submitted within one month.
- Enhanced cross-border cooperation – Strengthens coordination through EU-level information sharing and crisis management to address large-scale cyber threats.
- Stricter enforcement and penalties – Non-compliance can result in fines of up to €10 million or 2% of annual global turnover, reinforcing regulatory enforcement.
- Coordinated vulnerability disclosure – Establishes a framework for identifying and addressing cybersecurity vulnerabilities across the EU.
Implementation deadline: Member states were to transpose the NIS2 Directive into national law by October 17, 2024.
6. European General Data Protection Regulation (GDPR) and Cybersecurity
The General Data Protection Regulation (GDPR), introduced in 2016 and in effect since May 2018, enforces strict data protection laws across the European Union (EU) and the European Economic Area (EEA).
GDPR has a direct impact on cybersecurity, requiring organizations that collect, store, or process personal data to implement technical and organizational measures to protect against unauthorized access, breaches, and cyber threats.
Key cybersecurity obligations under GDPR:
- Data breach notification – Organizations must report breaches to data protection authorities (DPAs) without undue delay and, where feasible, within 72 hours. If a breach poses a high risk to individuals' rights and freedoms, affected individuals must be informed.
- Privacy by design and by default – Organizations must integrate data-protection measures into products and services from the outset, minimizing vulnerabilities.
- Secure data processing – Requires measures such as encryption, access controls, and risk assessments to protect personal data.
- Accountability and compliance – Companies must maintain records of processing activities (RoPA), conduct Data Protection Impact Assessments (DPIAs), and appoint a Data Protection Officer (DPO) if required. The appointment of a DPO is mandatory for public authorities and organizations whose core activities involve regular and systematic monitoring of data subjects on a large scale or processing special categories of data on a large scale.
- Strict penalties for non-compliance – GDPR adopts a tiered approach to fines. Fines can reach €20 million or 4% of global annual revenue, whichever is higher for more serious violations. While the less severe infringements can result in fines of up to €10 million or 2% of the company's global annual turnover, whichever is higher.
GDPR applies to EU member states and the EEA, which includes Iceland, Liechtenstein, and Norway. Companies operating in or offering services to individuals in the EEA must comply with GDPR, even if they are not physically located in Europe.
GDPR complements other EU cybersecurity laws such as the NIS2 Directive and the EU Cybersecurity Act, ensuring that personal data remains protected while organizations remain accountable for cybersecurity failures. It also aligns with the Digital Operational Resilience Act (DORA) for the financial sector, further reinforcing cybersecurity and risk management requirements.
7. DORA (Digital Operational Resilience Act)
Enforced in January 2023, the Digital Operational Resilience Act (DORA) establishes uniform cybersecurity and ICT risk management rules for financial entities, including banks, investment firms, insurance companies, payment service providers, and financial market infrastructures (FMIs). It aims to harmonize EU financial cybersecurity policies with global standards, strengthening resilience against cyber threats targeting the financial sector.
Key requirements under DORA:
- ICT risk management – Financial institutions must implement robust cybersecurity controls, including network security, threat detection, encryption, incident response, and access management.
- Third-party risk management – Companies must assess cyber risks from outsourced services, cloud providers, and ICT vendors, ensuring they meet strict security and contractual standards.
- Incident reporting – Financial organizations must provide an initial report of significant cyber incidents to regulators within four hours of detection and provide a detailed follow-up report within 72 hours.
- Operational resilience testing – Firms must conduct regular cybersecurity stress tests, vulnerability assessments, and advanced penetration testing (TLPT – Threat-Led Penetration Testing for certain high-risk financial entities designated by regulators) to evaluate their ability to withstand cyberattacks and maintain financial stability.
- Information sharing – DORA encourages financial entities to share threat intelligence and best practices to enhance collective cyber resilience across the sector.
DORA applies to all financial entities operating in the EU, including third-party ICT service providers. Its implementation deadline was January 17, 2025, however the regulation became enforceable on January 16, 2023, and requires firms to comply with strict ICT risk management and operational resilience requirements. Non-compliance may result in financial penalties, operational restrictions, or regulatory sanctions.
By integrating cybersecurity into financial regulations, DORA strengthens the EU's overall cyber resilience, ensuring the protection of financial institutions, critical infrastructure, and consumers against evolving cyber threats.
These regulations collectively enhance the EU's cybersecurity posture, ensuring the protection of businesses, critical infrastructure, and consumers from evolving cyber risks.
Scrut Automation's role in EU compliance management
Automating compliance helps businesses stay up to date with evolving EU regulations, reduce manual work, and ensure continuous monitoring.
Scrut streamlines compliance management by automating evidence collection, policy enforcement, and risk monitoring across various EU regulations. With AI-driven workflows, real-time alerts, and seamless integrations with cloud services, Scrut ensures enterprises stay audit-ready while reducing compliance efforts by up to 70%.

Ready to see what security-first GRC really looks like?
Ready to see what security-first GRC really looks like?
Ready to see what security-first GRC really looks like?
See what a real security- first GRC platform looks like
Ready to see what security-first GRC really looks like?
Focus on the traveler experience. We’ll handle the regulations.
Get Scrut. Achieve and maintain compliance without the busywork.
Choose risk-first compliance that’s always on, built for you, and never in your way.
Ready to see what security-first GRC
One platform, every framework. No more duplicate work.
You can’t manage user access if you’re always playing catch-up.
Explore the future of enterprise GRC
Tired of chasing vendors for risk assessments?
Join the thousands of companies automating their compliance with Scrut.
The right partner makes all the difference. Let’s grow together.
Make your business easy to trust, put security transparency front and center.
Risk-first security starts with risk-first visibility.
Secure your team from the inside out.
Don't settle for slow, expensive compliance. Get Scrut instead.
Risk-first compliance for forward-thinking teams.
Audits without the back-and-forth. Just seamless collaboration.
Scale fast. Stay compliant. Automate the rest.
Compliance? Done and dusted, in half the time.
Get ahead of GDPR compliance before it becomes a problem.
Outgrowing table-stakes compliance? Create custom frameworks with ease.
Navigate SOC 2 compliance, minus the stress.
PCI DSS compliance, minus the panic.
Take the wheel of your HIPAA certification journey today.
We’ve got what you need to fast-track your ISO 27001 certification.
Make your NIST AI RMF journey as smooth as possible.
Your GRC team, multiplied and AI-backed.
Modern compliance for the evolving education landscape.
Ready to simplify healthcare compliance?
Don’t let compliance turn into a bottleneck in your SaaS growth.
Find the right compliance frameworks for your business in minutes
Ready to see what security-first GRC really looks like?
Real-time visibility into every asset
Ready to simplify fintech compliance?
The Scrut Platform helps you move fast, stay compliant, and build securely from the start.
Scrut helps you set up a security program that scales with your business and stands up to audits. Without last-minute chaos.
Scrut helps you streamline audits, close deals faster, and stay ahead of risk without slowing down your team. Because trust shouldn’t take months to earn.
Scrut helps you set up a security program that scales with your business and stands up to audits. Without last-minute chaos.
Tag, classify, and monitor assets in real time—without the manual overhead.
Whether you're entering new markets or launching new products, Scrut helps you stay compliant without slowing down.
Scrut pulls compliance data straight from the tools you already use—so you don’t have to dig for evidence, chase approvals, or manually track controls.
Less manual work, more customizability. The Scrut Platform gives you everything you need to align your compliance to your business’s priorities.
With Scrut, you’re not just adding a tool to your offering—you’re adding a competitive edge. Join our Partner Network and help your clients streamline their GRC program.
Gaining trust is your first step to growing and cracking better deals. The Scrut Platform comes pre-built with all the tools you need to showcase a firm security posture and build confidence.
Don’t settle for rigid systems—Scrut ensures your risk management strategy is as flexible as your business needs.
Start building a security-first culture. Save your operations from improper training and a lack of compliance awareness.
Scrut fast-tracks compliance so you can focus on scaling, not scrambling. Automate compliance tasks and accelerate enterprise deals—without the grind.
Automate assessments, track compliance, and get full visibility into third-party risk—all in one place.
Scrut automates compliance tasks, supports proactive risk management, and saves you time, so you can focus on growing your business. Start building trust with customers and scaling confidently.
Leave legacy GRC behind. Meet the AI-powered platform built for teams managing risk and compliance in real time.
Give auditors direct access, keep track of every request, and manage audits effortlessly—all in one place.
Scrut ensures access permissions are correct, up-to-date, and fully compliant.
Whether you need fast results or a fully tailored program mapped to your risks and needs, Scrut delivers exactly what you need, when you need it. Ready to start?
Scrut unifies compliance across all your frameworks, so you can stop juggling systems and start scaling securely.
Manually managing your compliance processes and audits can get inefficient and overwhelming. Scrut automates these outdated, manual processes and eliminates your last-minute worries.
Access automated compliance, real-time risk tracking, and expert-backed support—all in one platform. Get started with Scrut!
Less manual work, more customizability. The Scrut Platform gives you everything you need to align your compliance to your business’s priorities.
The Scrut Platform helps you move fast, stay compliant, and build securely from the start.
Earn trust and back it up with solid evidence. Scrut takes you through the SOC 2 compliance journey step-by-step, navigating every complexity you face.
Manage your PCI DSS compliance with real-time monitoring and effortless automation. Get started with Scrut today!
Securing your PHI shouldn’t be a constant hassle. Scrut automates your workflows—from risk assessments to monitoring—so you can put your compliance worries on the back burner.
Automate security controls, simplify audits, and keep your ISMS aligned with the latest standards. Get started with Scrut!
Tackle potential AI risks with NIST AI RMF-compliant controls and get expert support every step of the way.
Offload the grunt compliance work to us. Execute manual, draining GRC tasks with the reliable AI-powered Scrut Teammates without switching contexts or bottlenecks.
Whether you're managing student data, partnering with educational institute, or expanding to new geographies—Scrut gives you the tools to stay compliant, manage risk, and build trust at every step.
Scaling healthcare doesn’t have to come at the cost of security. Scrut keeps your organization compliant, audit-ready, and protected—no matter how fast you grow.
Scrut automates the hard parts of compliance and security so you can move fast and stay ahead of risks from day one.
The Scrut Platform helps you move fast, stay compliant, and build securely from the start.
Growth in fintech comes with heavy scrutiny. Scrut helps you stay compliant, audit-ready, and secure—without slowing down your momentum.


















